1 min to read
Library

Starting with nmap scan gives only 1 port open.
nmap -T4 -p- -A 10.10.66.42
tarting Nmap 7.91 ( https://nmap.org ) at 2021-04-19 19:32 IST
Nmap scan report for 10.10.66.42
Host is up (0.48s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Admin Login |Library Management System
|_Requested resource was admin.php
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.85 seconds
Visiting the website running on port 80 gives a login page.
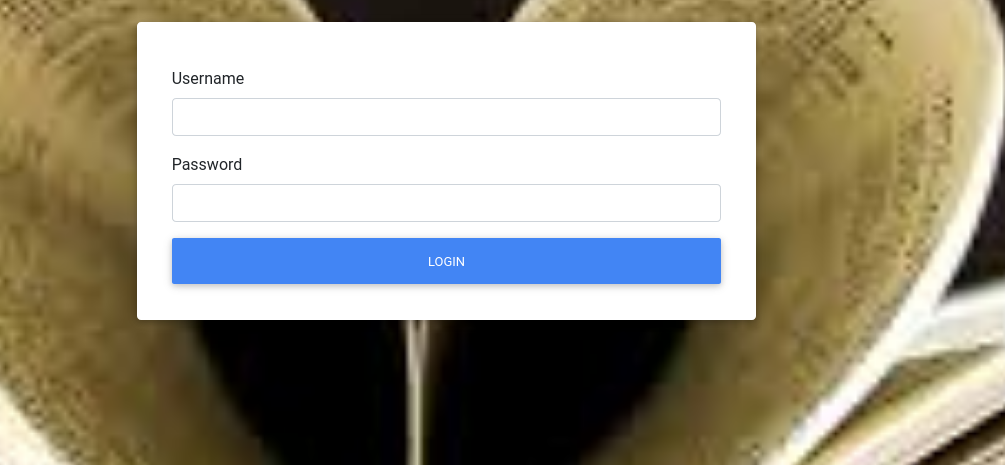
Trying some basic passwords reveals that username admin works with password as admin123.
This opens the website as administartor and under books dialog there is option to add new book which contains a field to upload image for the book.
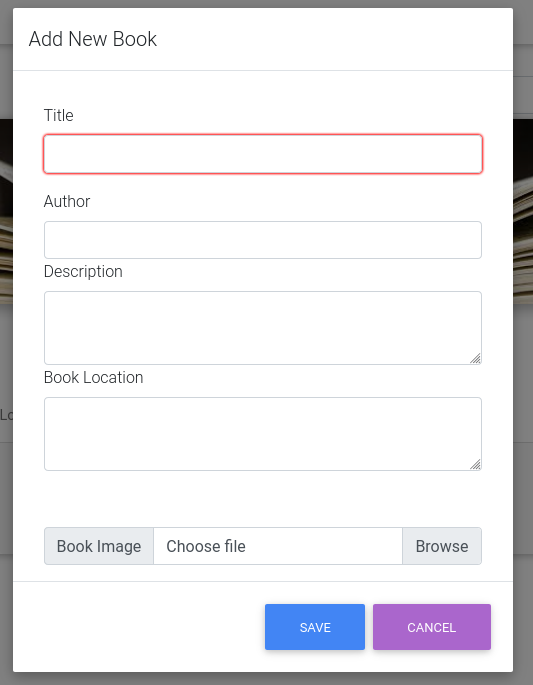
The field allows upload of any file, so upload a PHP reverse shell and upon inspecting the new created book’s HTML, the location of the uploaded reverse shell is present.
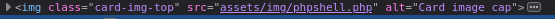
Requesting the file gives reverse shell as www-data.
Only 1 user is present on the system and trying to switch to the user with common passwords works as the password for the user is password.
Running sudo -l shows that the user has access to all commands on the system, basically he is the superuser.
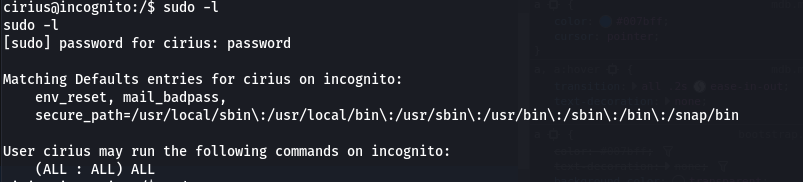
Change the user to root using sudo su -